Step 3: Discover and Prioritize Technology Obsolescence Risks
Analyze and prioritize technological risks using insights obtained from reports.
When you have built sufficient data for a meaningful analysis, use reports and diagrams to analyze and prioritize technological risks. The Technology Risk and Compliance offers additional views in the reports for better insights into underlying risks. Here are a few illustrations of using reports to assess risk:
-
In the Application Landscape report, apply the Obsolescence: Aggregated Risk view to see how outdated IT components impact the business by aggregating their obsolescence risk onto the application layer. The color-coded view effectively illustrates which applications have unaddressed risks.
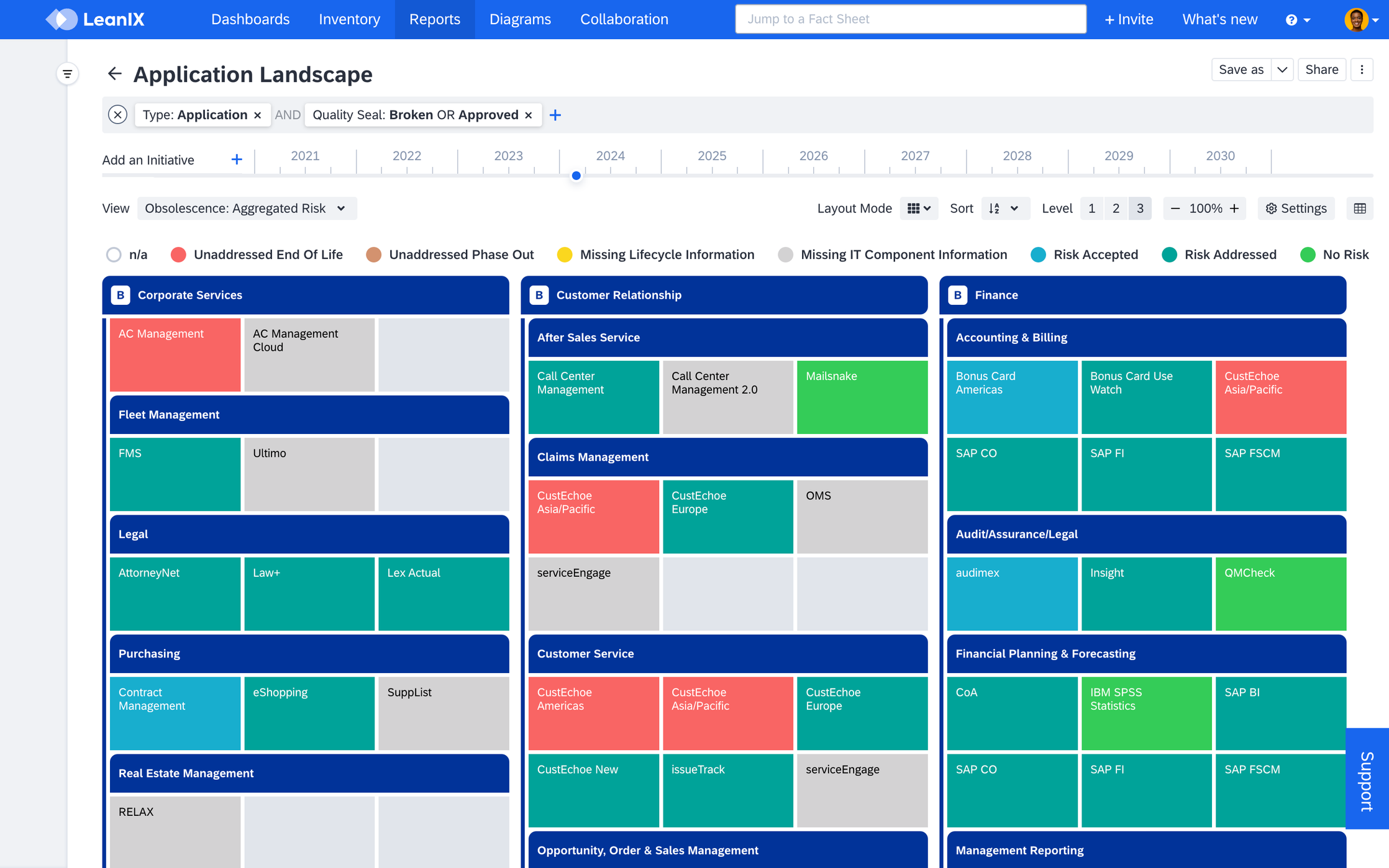
Obsolescence: Aggregated Risk View in Application Landscape Report
-
From the report’s Settings, cluster the applications by their Business Criticality. This easily helps you distinguish which applications pose the most immediate and potentially business-disrupting threat. Understanding this helps prioritize which obsolescence risks to address first. You can use the time-slider to see what applications and their underlying IT components change lifecycle phase in the next fiscal year and already also require attention. This aids in budget planning purposes. In the example below, applications Cost Modeling and Contract Management not only have unaddressed end of life risks but are also facing phase out risks by the end of the year 2025.
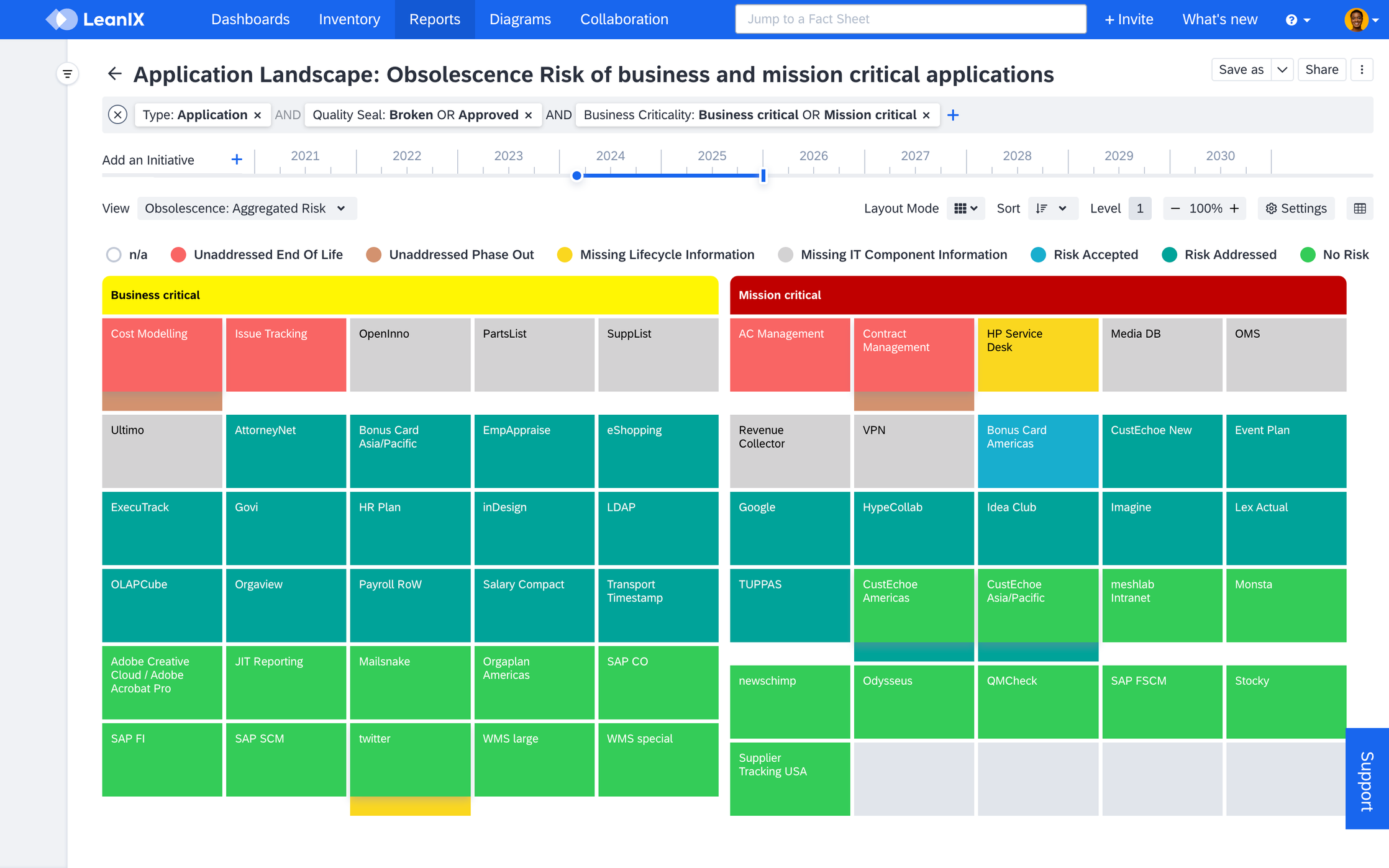
Applications Clustered by Business Criticality in Application Landscape Report
Best Practice
- Focus on ‘end of-life' risks first before addressing IT components that are in a 'phase-out’ state.
- Use business criticality, lifecycle state, successor, business context, time horizon, cost to prioritize applications for evaluation. This targeted approach allows for manageable goals, allowing for quick wins and gaining additional stakeholder buy-in and support for your initiatives.
- Make use of tags or create a custom field to capture the priority of each identified risk. For guidance on when to use tags versus custom fields, see How to Use Tags vs. Custom Fields.
-
-
Within the report, select the application to open the side panel and find out which IT components support the application and what their obsolescence risk statuses are. These insights equip you to reach out to the application owner and define a transformation path for addressing IT components with unaddressed end of life statuses.
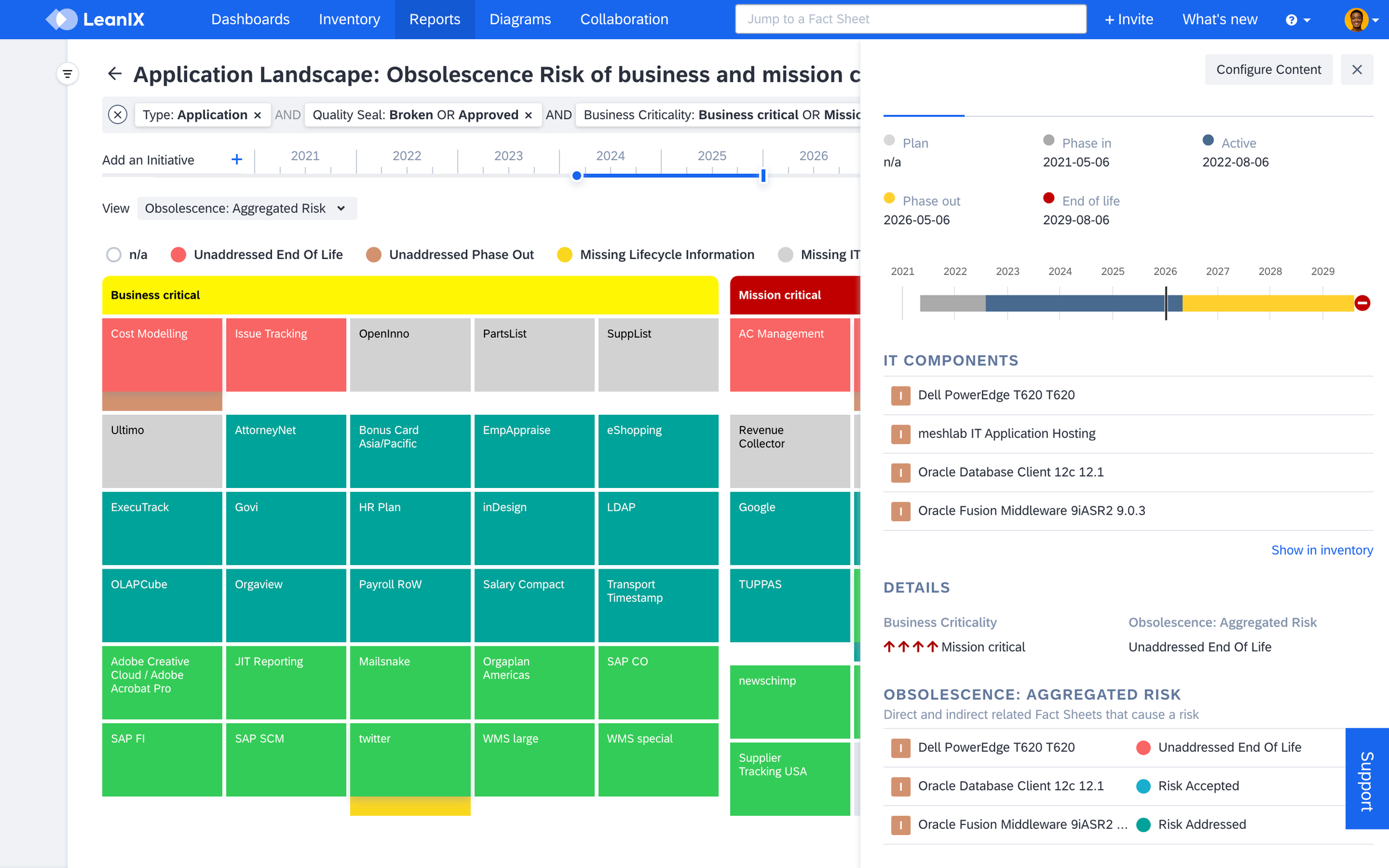
Obsolescence Risk Details Accessed in the Right Side Panel
-
Leverage the IT Component Roadmap report to track the lifecycle of IT components and anticipate potential risks in advance. From the report Settings, cluster the IT components by Application and apply the Lifecycle view. You can filter to focus on Phase out or End of life states effective in the future. This enables you to monitor phase out and end of life risks on an ongoing basis and plan mitigation measures accordingly.
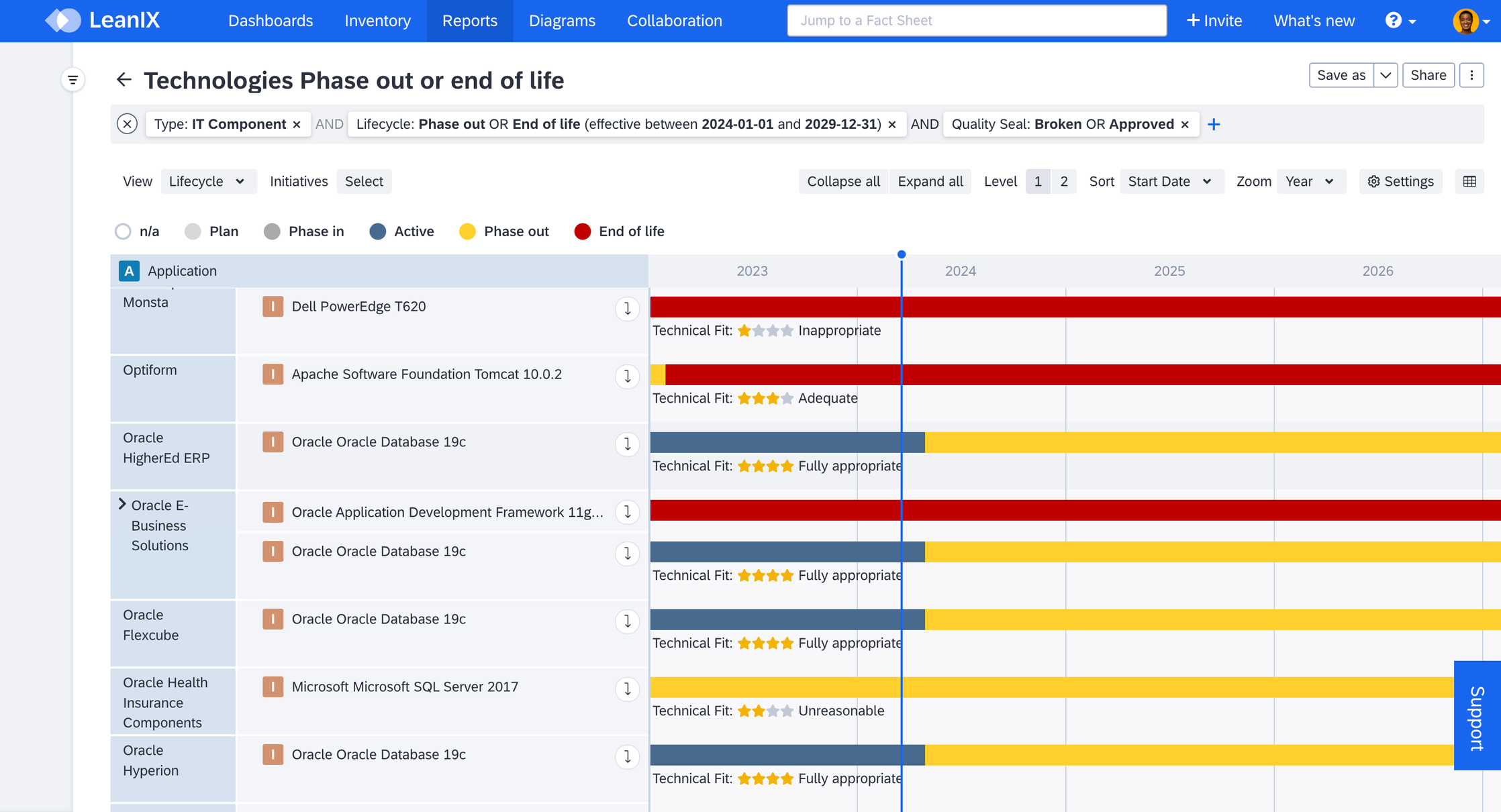
IT Component Roadmap Report with Lifecycle View
-
While prioritizing risk mitigation efforts based on business-critical applications is effective, you can also consider additional factors for more advanced insights. This could be focusing on IT components that impact strategic concerns, business capabilities, business units, revenue, or customers among others.
This enables the translation of technical debt into business impact at a strategic level more concretely. However, achieving this requires mature data on costs, processes, data, and their relations mapped to organizational objectives and strategic goals. It is essential to consider whether the insights gained from analyzing this data justify the resources and time invested in collecting and maintaining it.
Step-by-Step Guide
Updated 30 days ago
